“At least S$764,000 lost in September to e-commerce phishing scams in S’pore”, “378 people fell prey to phishing scams in the first half of November”. Do these headlines scare you?
You think to yourself, why are so many people falling for these scams? Are they not very well informed? Or are the attacks so sophisticated that people can’t distinguish real websites from malignant ones?
Well, both are unfortunately key reasons why scams of this scale occur in our largely highly educated populace.
Let’s take a look at some examples.
Case Study 1: signpost.one (Threat level: 8/10)
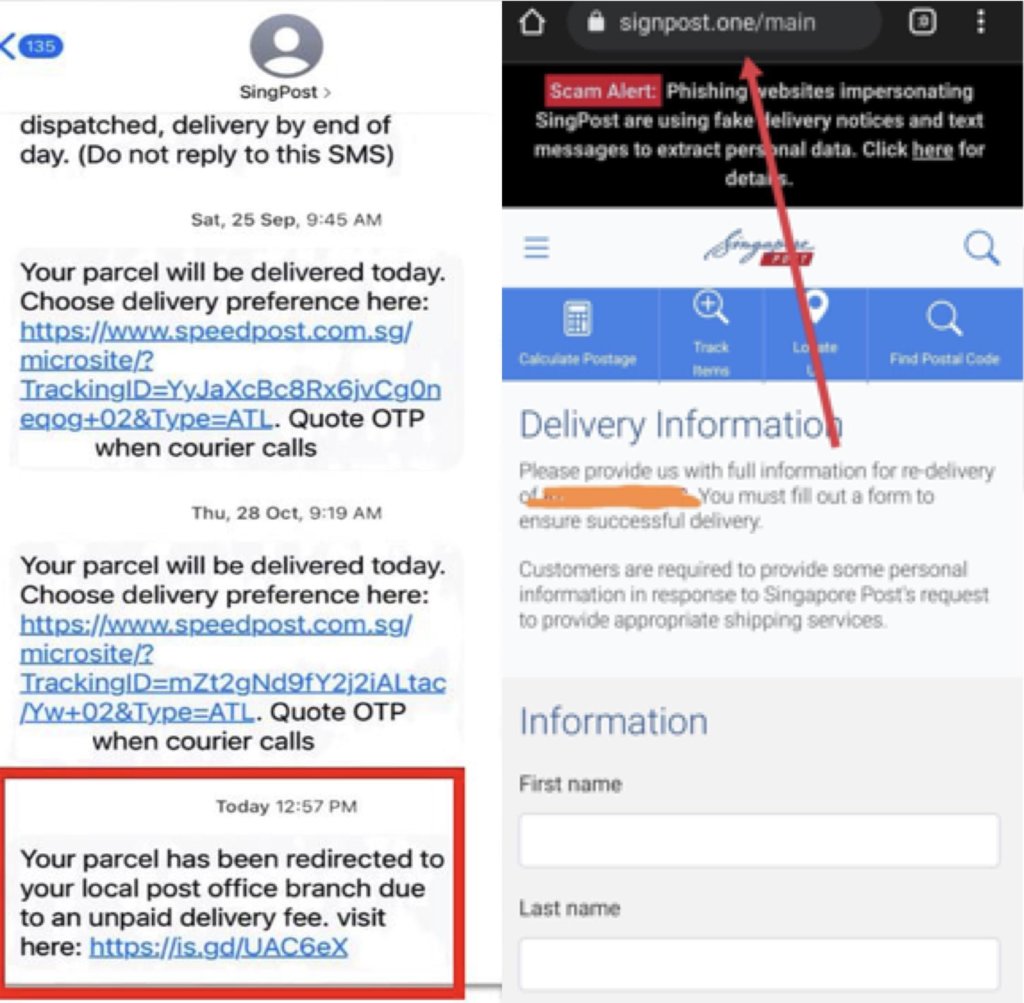
You receive an SMS from Singpost, in the same chat that you usually receive your updates from claiming that your parcel has been redirected to your local post office branch due to an unpaid delivery fee.
Out of curiosity, you click the link and land on a legitimate looking website of Singpost that even has an advisory telling you to avoid phishing sites.
Due to your vested interest in getting your parcel out of the post office branch, you ignore the most glaring red flag that has been in front of you for 1 minute or so. That url reads signpost.one, not singpost.
You carry on entering your personal details and address and end up on a page prompting for a payment for a DHL delivery as normal Singpost deliveries are unavailable.
One of 2 things can happen to you.
You eventually found it weird that Singpost uses DHL and leave the site, so you only gave away your address and number.
Or if you carry on letting “DHL” deliver your parcel, you’ll be directed to pay a nominal S$3 delivery fee. If you enter your credit card details into the payment gateway, you are in trouble.
You have successfully handed over your name, address, contact and full credit card information to the scammers. It can cost you a pretty penny, depending on your credit card limit. Yikes.
Case Study 2: security-dbs.com (Threat level: 5/10)
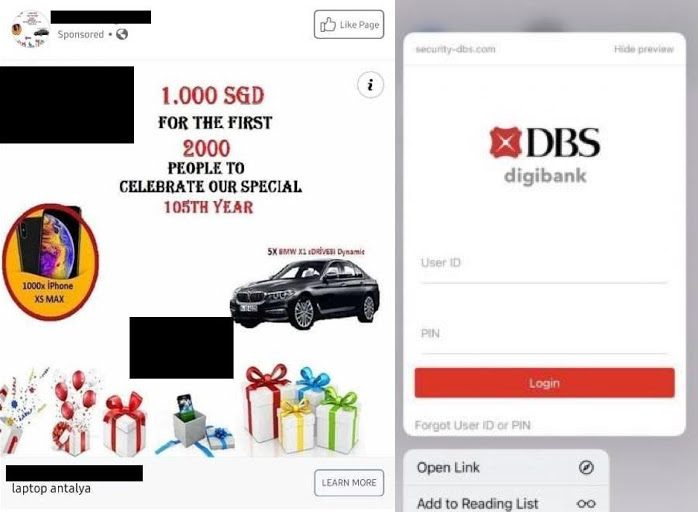
This phishing attempt is kind of a low level one, but is surprising some people fall for it. So you’re scrolling through your Instagram or Facebook feed until a poorly designed ad by “DBS” pops up.
This Ad claims to give “1.000 SGD FOR THE FIRST 2000 PEOPLE TO CELEBRATE OUR SPECIAL 105TH YEAR”, along with 1000 sets of iPhone XS Maxes.
If you click on the learn more button, you get brought to an again, legitimate looking DBS site, prompting you to log in,
If you enter your credentials, the website will pretend to load for a bit, while they use that information to log into the real DBS portal.
The site will then prompt you to enter an OTP that you receive from DBS (the real one). After entering the OTP, the site will pretend to load again while the scammers log into your account to siphon money out of your accounts.
But there are more
These examples are just scratching the surface of the types of phishing scams available. But there are lessons to learn from them. Read on to find out 4 ways to spot these attempts and how to avoid them.
Check the Url
The first and most obvious way to spot a phishing attempt is checking the Url provided in the email or message.
99% of legitimate messages from companies do not use shortened urls like “is.gd/phishing-site” or “bit.ly” when prompting a response from you.
If DBS sends you a link, chances are it will be dbs.com.sg/somesite, and if Singpost sends you a link, it will be singpost.com/somesite, simple as that.
But if you clicked on the shortened url, fret not as the full url of the page will be revealed once the page loads.
Once you see the full url in your address bar, open your eyes wide and start checking the spelling.
Scammers likely buy up misspelled domains of official ones like “signpost.com” and “internet-baking.dbs.com.sg” to mislead you into thinking you are on the official site.
Mind you, domains are dirt cheap at S$20 a year and a ludicrous number of options are available to pick from.
A quick look on Google Domains show that anyone can buy “dbsbaking.com”, copy the html on the actual DBS site, and host it using their newly acquired domain in a matter of minutes.
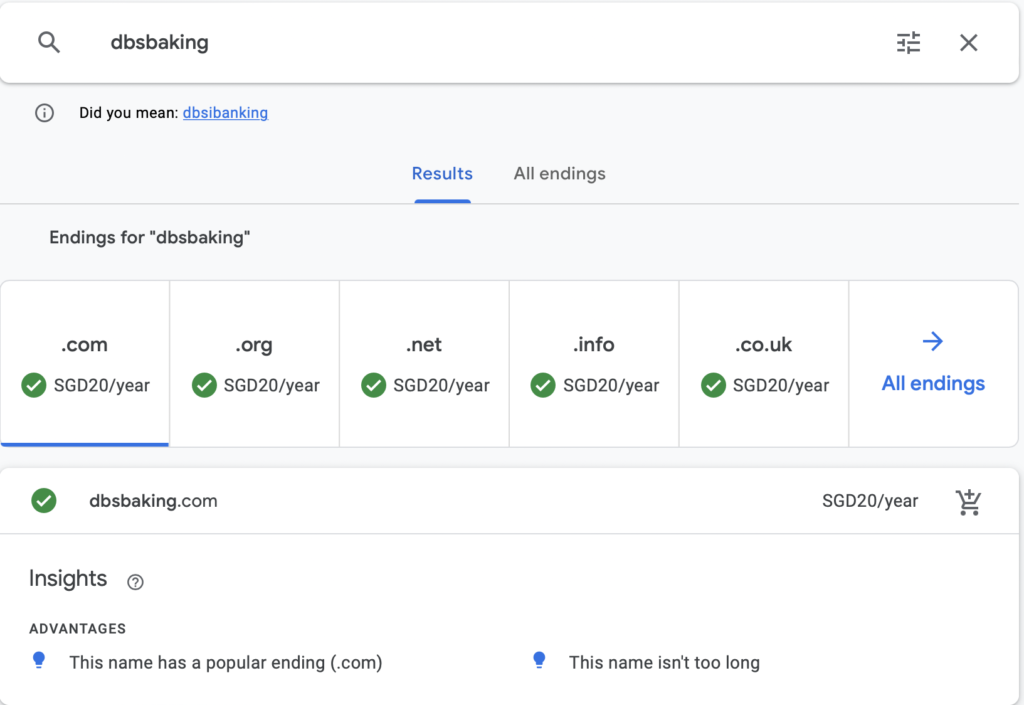
Remember, analyse the url intently to check for any misspellings as this will be your first line of defence.
Check for Grammar
You may think that scammers should use perfect grammar to convince people they are legit or official. But this is rarely the case.
See, if they use perfect grammar, more people with low propensity to fall for scams visit the scam sites to interact with the forms and payment gateways. This can lead to higher rates of spamming or abusive behaviour on their site once these people realise the site is a sham.
The logic is if someone is careless enough to ignore the obvious grammatical errors, they are less likely to be wary of the malignant website, and are more prone to entering their payment details.
By only targeting the lowest common denominator, the scammers can efficiently focus their resources for greater social engineering.
So, don’t be a part of the group, check for the proper use of English before clicking the link.
Check for SSL Certificates
Secure Sockets Layer Certificate, or SSL certificate is a proof that the website is using an encrypted link between their server and the browser. Your address bar should show a lock icon.
If “Singpost”, “DHL”, or “UOB” sends you a link that does not have a lock icon when loaded, it is an immediate red flag.
Without SSL certificates, everything you enter is available for anyone with an internet adapter to intercept in plain text.
However, the absence of SSL certificates being a key determinant of a phishing site has diminished over the years. Almost all web hosts now, shady or not, provide SSL certificates to any site that pays them.
This means that my theoretical “dbsbaking.com” site can obtain an SSL certificate without any hiccups.
Thus, other methods of identification used in this blog should be used in tandem with checking for the presence of SSL Certificates to prevent scams from happening.
Test payment gateway with Test numbers

This is a tricky one, while most phishing sites just copy the look of credit card payment gateways to steal your card details, some sophisticated sites utilise checks that ensure your card is real.
Let’s break down the first case, when the look of the gateway is replicated. These forms usually don’t come with checksums to check if the card details you provided are real or not.
One thing you can do if you are still unsure if the site is real, enter a random 16 digit number, cvv and expiry date to submit the payment.
If the site says that your payment is successful, cheers to you, you avoided a scam.
But if the site says that your payment failed due to an invalid card number, you may start to self doubt and enter your actual card details. Do not do that.
Instead, enter one of the test card numbers provided by Visa: 4111 1111 1111 1111 and try again. Most likely, the sophisticated site implemented the Luhn algorithm to check if your card number is valid.
This Visa test card number passes the Luhn algorithm, which means it checks off one of the boxes for a successful payment.
Other boxes that need to be checked are the validity of the expiry date, cvv and the balance of funds on your card.
If the test card number passes the payment gateway even with random cvv and expiry date, close shave, you didn’t get phished.
The reason why official payment gateways are not used on these sites is due to regulation.
For an entity to collect payments online from a site, it has to provide proof of identification and a working bank account to receive funds. Obviously, scammers won’t want to do that.
Conclusion
Like I just discussed, it is really easy for anyone to buy a domain and host a malicious site resembling official ones.
To recap,
1. Check the url to see if it is misspelled
2. Check for the use of proper grammar
3. Check for an SSL certificate
4. Always provide the payment gateway with test numbers if in doubt
While it is unfortunate that an increasing number of people are falling for these scams, I believe with enough education and awareness, we can stop such incidents from happening.
Share this knowledge with your friends and family who are not as digitally savvy, correct them when they misplace their trust in these scammers.
Do you have any tips to spot phishing attempts? Share them in the comments below.
Derrick (Yip Hern) founded Tech Composition to provide valuable insights into the tech and finance world. He loves to scour the web for the best deals and embark on software projects during his free time, a typical geek, right?