Scams and hacks are more common than ever in this digital age, especially for Singapore, a country with a high smartphone penetration rate. You may have heard of the recent Carousell phishing scam that had victims lose about S$1 million in total, or the high profile S$13.7 million OCBC phishing scam and thought to yourself: How can I prevent this?
Even as companies and the government scramble to prevent such scams from happening again, it is simply impossible for them to plug every single hole. When there’s financial incentive involved, scammers will keep coming up with new schemes to cheat your hard earned money.
The onus therefore lies heavily on the users: me, you, our parents, to be aware of dubious practices and take measures to prevent scams from happening. Regardless of how confident you think your digital literacy skills are, it doesn’t hurt to have a recap on the 5 cybersecurity tips every Singaporean should know about in 2023.
- Check the URL
- Set Easy to Remember, Unique Passwords For All Accounts
- Never Install Apps From Unknown Sources
- Never Click On Dubious URLs Even If You Think It Doesn’t Do Any Harm
- Familiarise Yourself With The Latest Scams And Preventive Measures
- Conclusion
- Get the latest in Tech with a Singaporean take, right on Telegram.
Check the URL
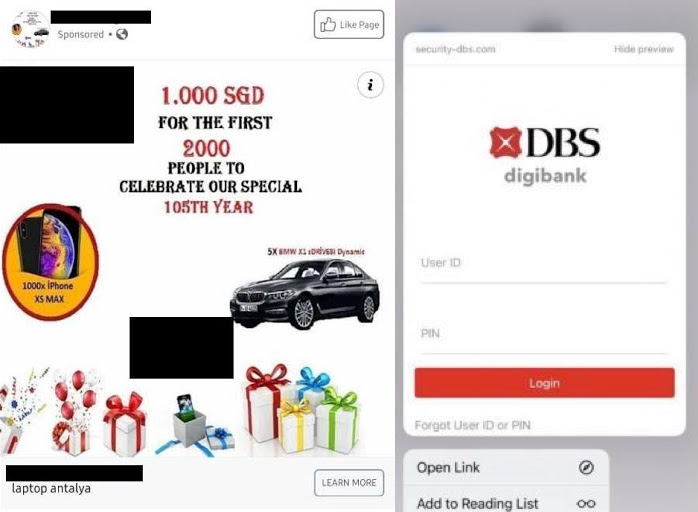
I’m going to start with the easiest one, checking the URL. Anyone with basic web programming knowledge can extract the source code of any website, modify it, and serve it on the open internet within minutes. The implication of this? Cloned sites that look exactly like that of your bank or app.
In the above image, you see a DBS login page that looks exactly like the official one, except the domain reads security-dbs.com. This is a tricky one though, since “security” in the domain can be misinterpreted as a subdomain of dbs.com.

A subdomain is a “add on” page for a given domain, like docs.google.com (Docs), or maps.google.com (Maps), or mail.google.com (Gmail). These subdomains are denoted by the “.” notation and nothing else. In DBS’ case, one of its pages is internet-banking.dbs.com.sg, where internet-banking is the subdomain, and dbs.com.sg is the domain.
In the same example, security-dbs.com.sg may look authentic, but notice how security and dbs.com.sg aren’t separated by a “.” like regular subdomains should? Turns out, there is no subdomain on the site, and the domain is entirely security-dbs.com.sg, which is definitely not the official dbs.com.sg domain name.
It must be emphasised that literally anyone can purchase “security-{bank name}.com.sg” from a registrar. Heck, even I can buy security-dbs.com.sg for $45 after a quick search on Google and host my very own website on it.

So how can you avoid this? Ever since the OCBC phishing scam, the Monetary Authority of Singapore has come up with a new rule banning all local banks from including clickable links in messages or emails to customers. So any “bank” prompting you to “dispute a transaction” with a link will definitely be a scam.
But that doesn’t solve everything. This rule isn’t applied to all local businesses and you should still take note of how to discern between domains and subdomains, as well as keep your eyes open wide to check for misspellings.
Set Easy to Remember, Unique Passwords For All Accounts
Other than being discerning with URLs, it is also important to set unique and secure passwords for all of your accounts. Yes, all. If you reuse the same password on every single site you have, it won’t matter how secure that one password is if it is vulnerable to a single point of failure.
Every time you create an account with a service, you are assuming that the service provider has in place database security, and strong enough encryption to keep your passwords safe. Most reputable companies convert your plain text password into irreversible gibberish using a process called Salting and Hashing.
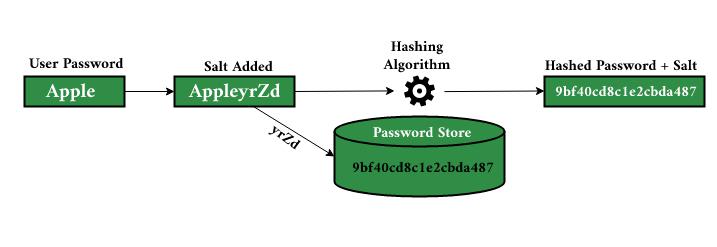
A “salt” is a randomly generated short phrase that gets added to your plain text password before it gets processed by an irreversible hashing algorithm. But why do we even need a “salt” if the algorithm is irreversible?
This is because users really love to use common passwords like “password”, “123456”, or even “PassW0rd123”. Hashing algorithms are deterministic, meaning the same plain text passed to it will always generate the same hashed result.
Bad actors can easily obtain hashed passwords of common passwords by running them through common hashing algorithms, and compare those hashed passwords against leaked data online. If they find a matching hashed password, chances are, they can access that account easily.
Salting mitigates this issue as it adds some random complexity into the plain text password, generating a different hashed result even if more than 1 user has the same password. It’s a fairly standard practice, but we shouldn’t assume every service provider that you signed up with has this in place.
You will never know if a company is storing your passwords in plain text without any encryption, leaving the door wide open for a full on takeover of all your online accounts if their database gets compromised.
That is why it is paramount to have unique yet easy to remember passwords for every site, and I have the perfect guide for that:
Never Install Apps From Unknown Sources
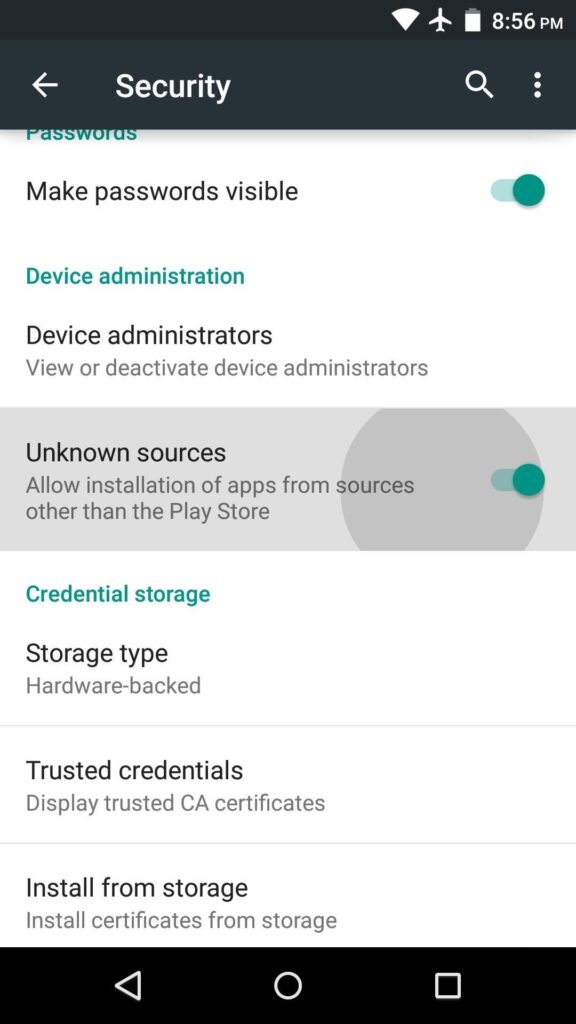
Ever wanted to obtain a paid app for free and turned to third party websites? That’s probably the easiest way to get your device infected with malware. See, some of these third party apps aren’t so generous to simply provide you a subscription-free copy of Photoshop at no cost.
What some malicious actors may do is modify the source code in the Android Package File (APK) or desktop executable file to embed viruses and keyloggers. The best part is, you won’t even know about these changes in the code while you’re happily editing your selfies on the unofficial app.
Even if you didn’t intend to save a few dollars by bypassing the app store, you can still be a victim of such scams if the official site provides an APK install option.
Very recently, Bitkeep, a Singaporean Defi Crypto Wallet provider was targeted in a hack that had users lose S$10 million in crypto. What happened? Well, Bitkeep offered Android users 2 ways of installing the wallet app: through the Google Play Store, and through an APK provided on their official site (with the correct URL).
This is quite unusual for an app developer to do, but nothing seemed malicious. This set the stage for a hacker to exploit this unusual method of app distribution. By rerouting the APK download button on the site to an APK that was modified by him, he was able to remotely obtain users’ crypto private keys.
Using these private keys, he syphoned off crypto in affected user wallets and disappeared. So the lesson here is to install apps only from the App/Play Store for mobile devices, and official reputable sites for desktop users.
Never Click On Dubious URLs Even If You Think It Doesn’t Do Any Harm
The rule of thumb is to never click on any suspicious links ever. But if you ever just wanted to peek behind the curtains of a suspicious link by clicking it, please don’t. Here’s why.
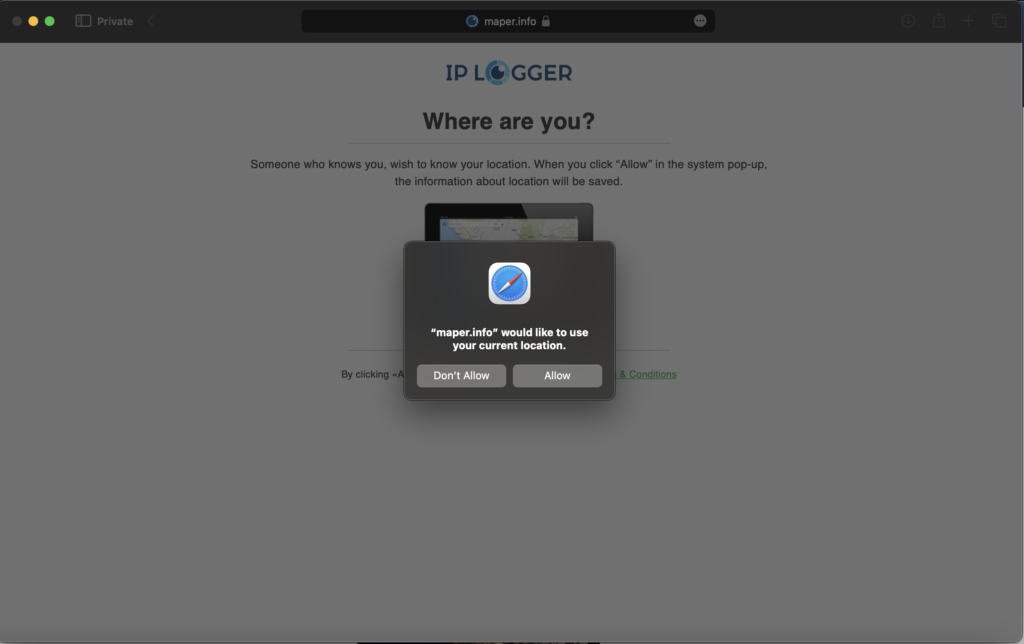
There exists a class of URLs that function as IP Loggers, usually found in social media and ecommerce outbound links to capture your IP address for analytics purposes. But these IP Loggers can be used for way more malicious stuff.
Using a utility website like iplogger.org, I was able to generate links that directed users to a warning site that asks the user for permission to disclose their GPS location. As a legal service, they were required to warn the recipient about the data that might be collected by a bad actor.
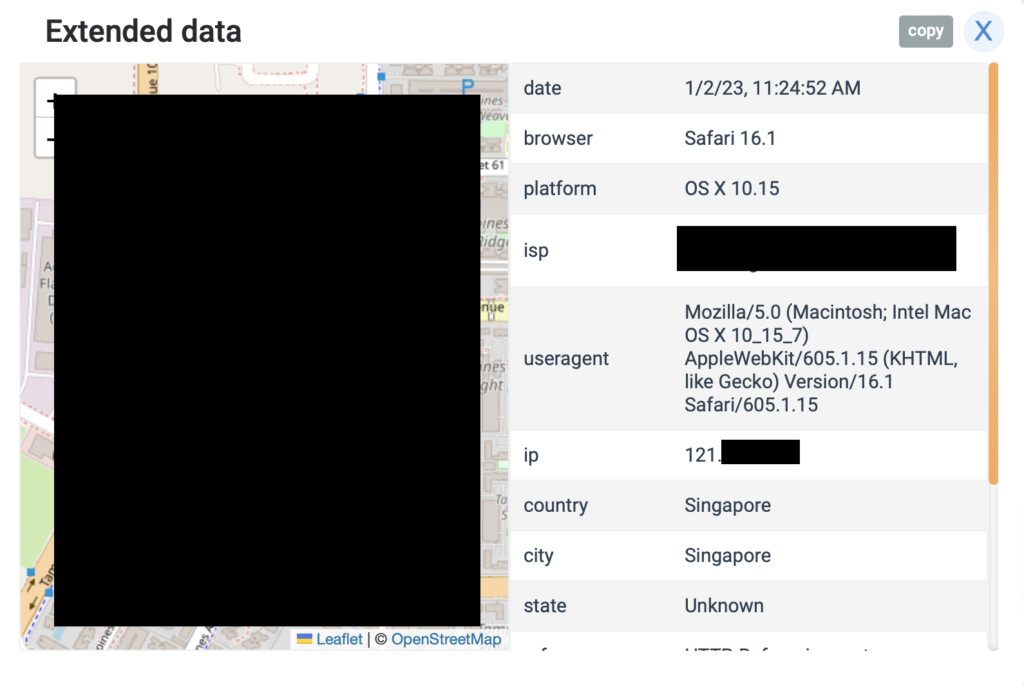
As I created the link myself, I hit allow location, and was redirected to google.com as if nothing happened. On the other end, I obtained precise location information, platform, internet service provider name and IP address of my recipient (me).
If you thought this is scary, wait till you find out that similar services like IP Logger exist, and are used illicitly to phish location information without a warning page. For example, a commonly misspelt domain name of a food delivery service can be bought and the website is loaded with Ip logging code.
When the user clicks on the URL, he is shown a cloned webpage of the food delivery service and prompted to share his location for nearby restaurant options. Once he clicks agree, the person on the other end will obtain his exact location at that given moment.
Social engineering is often used by hackers and malicious actors to propagate these links. Stay safe and never click on links that seem suspicious. Use my first tip on checking the URL to be doubly sure.
Familiarise Yourself With The Latest Scams And Preventive Measures
The best way to internalise these cybersecurity tips is to keep abreast of common scams that are circulating locally. Fortunately for Singapore, the government maintains a comprehensive scam advisory site, ScamAlert for potential victims to seek assistance, and for public education.
Other than ScamAlert, you may want to keep your eye out on social media for accounts about new types of scams. You may also want to keep the less digital literate seniors in the loop by informing them about these frauds

One of the easiest and most effective ways to prevent local scams is by simply installing ScamShield. ScamShield operates a central database managed by the Singapore Police Force to compare against the incoming phone number. If the number in question made to you is in the database, the call will be blocked.
For SMS, ScamShield filters spam messages made by people not in your contact and stores them in a junk SMS folder for you to view them if needed. This way, the number of spam calls and messages may decrease dramatically.
Conclusion
Whether you like it or not, scams and hacks are part and parcel of our digital lives as we progress with new technologies and systems. But with the above cybersecurity tips that you just learned, like checking the URL and subdomain, setting unique passwords for every account, never downloading apps from unknown sources, you will probably be much less prone to frauds.
Staying in the loop about recent scams, and educating your loved ones about them will also aid the reduction in hacks, perhaps even reducing the financial incentive for these bad actors in general. Do you have any cybersecurity tips that you feel needs to be added on to this list? Leave them in the comment below.
Derrick (Yip Hern) founded Tech Composition to provide valuable insights into the tech and finance world. He loves to scour the web for the best deals and embark on software projects during his free time, a typical geek, right?






I do agree with all the ideas you have introduced on your post They are very convincing and will definitely work Still the posts are very short for newbies May just you please prolong them a little from subsequent time Thank you for the post
I do agree with all the ideas you have introduced on your post They are very convincing and will definitely work Still the posts are very short for newbies May just you please prolong them a little from subsequent time Thank you for the post